Important Safety Tips while Using Public WiFi
You do not have very go far these days to access free public Wi-Fi. It is available in airports, libraries, cafes, hotels and government buildings. This is helpful but it is important for both adults and kids to make sure they do not trade safety and security for convenience. Just because the public building you are in is reputable, does not mean the Wi-Fi connection is secure.
When using your smart phone or computer in a public hotspot, you need to be careful to ensure the Wi-Fi network is encrypted. Otherwise, it opens you up to the risk of having your online accounts hacked. This could result in cyber thieves stealing your personal information.
Here are two basic safety tips to keep in mind to protect your information. And then we will explore additional ways to stay safe while online in public.
1. Check if the Public Wi-Fi Network is Secure
As mentioned, we are not worried about the people who control the Wi-Fi network. The risk is when others around us are in the business of hacking into the personal accounts using the network. safety-tips-that-both-adults-and-kids-need-to-know-while-using-public-wifi/ It could be the person sitting across from you in a coffee shop, or just outside on the street.
If the public Wi-Fi network does not ask you to enter in a WPA or WPA2 password, the network is not secure. As you are probably thinking, this is most places. The most common public Wi-Fi networks that require a password are internet providers with home you have an account.
2. Ensure the Websites You Visit Show https
An example of this is https://youraccount.com or https://yourbank.com. Secure websites will encrypt your information as you use the site. Unsecured sites do not have the “s” in them, such as http:// (your information is not encrypted and kept safe if you don’t see the “s”)
Unsecured websites will also show a padlock that is unlocked. Here is an example of what a secured website looks like. Notice how with website URL with https also has a closed lock.
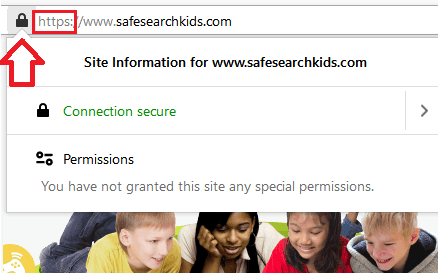
Clicking the lock will reveal more information about the secure site. Now you can be sure you are on a secured website.
On a mobile website, it will look like this.

If you are using a site that is not secure and locked, you open yourself up to hackers that can access your personal accounts and steal your data. This could mean your name, address, phone number, address book and photos.
Hackers need to see you on a public WiFi to be able to monitor your activity, so one sure fire way to to prevent this (regardless of being on an unsecured network) is to encrypt your data by using a VPN. It can be turned on when you wish, such as when you are in public or traveling.
Here are more ways to protect your personal information when using public Wi-Fi.
- It is good idea to have different passwords for each of your online accounts. This way if a cyber thief gets a hold of your email and password on one of your accounts, they will be unable to log into other accounts using the same password.
- Educate yourself on the various ways cyber attacks happen even when you are in the safety of your own home network, such as Phishing, Vishing and SMishing. Hacking through public WiFi is less common than these other methods used.
- Do not email important information about yourself for any reason. This includes credit card details, bank account information and your personal government ID number. You should never do this even if a network is secure, not even from home.
- Use a mobile proxy to mask your IP address and when accessing accounts in public, whether it is your own computer or a PC in a library, always log out when finished.
- Take advantage of 2 step verification methods being offered within your personal accounts. This will add further security because 2 step verification means you cannot log in until you enter a secret code that is sent to you by text or via the Google Authenticator App.
Proper Online Activity When Using Public Wi-Fi
If you are in doubt about the security using any public Wi-Fi network or website, it is best to restrict your activity online to general use, such as searching Google while you are not logged into your Google account.
Do not log into any personal accounts and if you find it necessary to do so, disconnect from Wi-Fi and use your personal cell data. Even then, it is always important to ensure the websites on your account pages start with https in the URL. Most major accounts websites are secure, but if you do not see https something may be wrong.
If you are in doubt about the security using any public Wi-Fi network or website, it’s best to restrict your activity online to general use, such as searching Google while you are not logged into your Google account.
Don’t log into any other personal accounts and if you find it necessary to do so, disconnect from Wi-Fi and use your personal cell data. Even then, it’s always important to ensure the websites on your account pages start with https in the url. Most major accounts websites are secure, but if you don’t see https something may be wrong.
Beware of Evil Twin Attacks
What does this have to do with protecting yourself on publish Wi-Fi? Well, an Evil Twin Attack happens when a cybercriminal sets up a Wi-Fi network that mimics a legitimate one. The goal is to trick you into the log into the wrong network by mistake.
Unsuspecting victims will think they have connected to the “safe dedicated network” associated with the public area they are visiting. Scammers and then can steal your information or infect your devices.
Captive portal pages can also be used by hackers to funnel you to malicious websites or infect your device with malware.
Red Flags to Look Out For
Seeing multiple networks with similar names should raise suspicion. Stay alert for security notices on your device. It will often let you know if you’re about to connect to an unsecured network.
These networks are dangerous because there are no built-in security protections to keep hackers out. Using your personal data or a friend Hot Spot is a safer alternative when you encounter unsecured public Wi-Fi networks.
Additional Resources:
- Now that you’ve read about public WiFi safety, learn about WiFi security on your home network.
- Learn how to protecting your family from identity theft while traveling.